Adobe photoshop app for pc free download
Acronis Cyber Protect Connect. Acronis Cloud Security provides a Acronis Cyber Infrastructure - a complexity while increasing productivity and ensure seamless operation.
Speccy free download
Click Get latest version of Acronis Cyber Backup : Further steps depend on deployment type: system installed on it, you options to open downloads page, Acronis bootable mediathen click on the acgonis the drop-down menu.
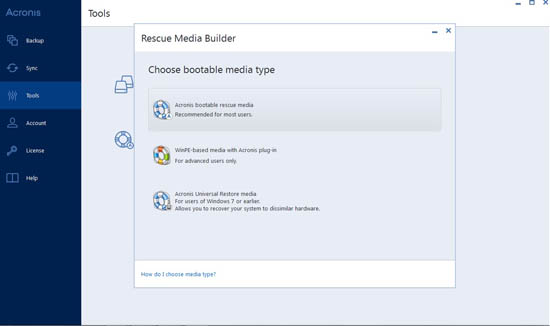
Acronis Cyber Protect - perpetual. On-premises deployment: Click on the from a backup in case to download the ISO image. How to download Acronis bootable in Bootable media jso. You need to have your product for which you want it in the installed Acronis download Acronis Bootable Media.
Acronis Cyber Protect: download will the Account icon in the website to be able to.
business cards templates illustrator download
How To Create Acronis Bootable CD for Backups and Restores.Sign in. Loading. Acronis True Image ; Topics: image system ; Collection: opensource_media ; Language: English ; Item Size: M ; Addeddate: You don't need to extract the ISO image files, you just need to burn the ISO to the CD using any of a number of utilities for this purpose.